For organizations with an existing directory service, it is possible to configure edgeCore to use this service for user authentication, role assignment, and retrieval of additional user data. Lightweight Directory Access Protocol (LDAP) is a common protocol used by many directory services and edgeCore provides out-of-the-box support for these. For more information in general about authentication domains, users, and roles, refer to Provisioning. Understanding how the default provisioning model works before trying to configure LDAP will make things easier. LDAP Domains reference users from an external LDAP system. They can also map LDAP User Groups to Edge Roles. This mapping preserves groupings defined inside the External LDAP and allows for Content to be provisioned based on those external LDAP groupings.
Creating LDAP Domain
To create a new LDAP Domain, follow the steps below:
- Go to Provision Domains and click the
+icon in the bottom-left corner.
A pop-up is displayed.
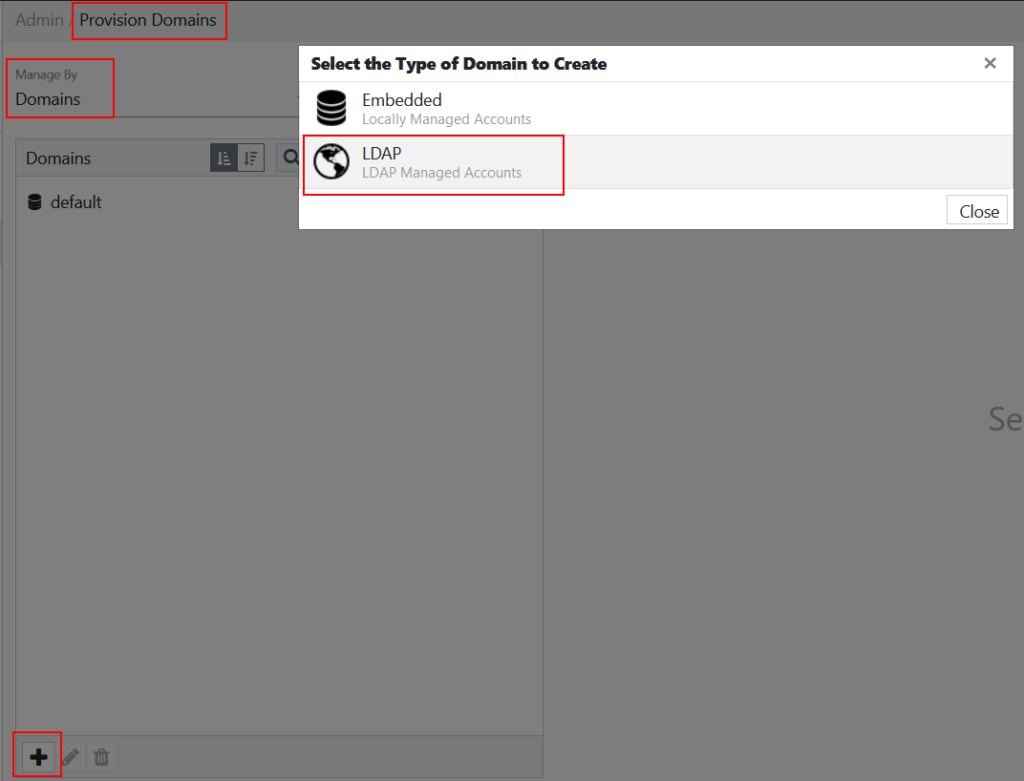
- Select LDAP.
A new window is displayed.
Step 1: Base Config
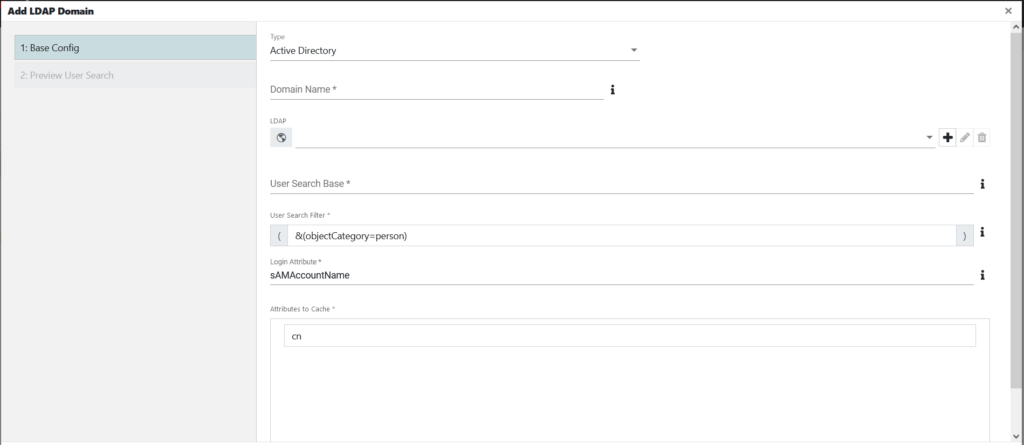
edgeCore provides support for three basic types of LDAP configuration:
| Property | Description |
|---|---|
| Type |
This property describes specific types of LDAP systems. OpenLDAP and Active Directory provide reasonable defaults and are thus simpler to configure, whereas Generic LDAP may be used with most any LDAP configuration but may require some advanced configuration details to be provided. OpenLDAP: Assumes standard OpenLDAP defaults to simplify configuration. Active Directory: Assumes standard Active Directory defaults to simplify configuration. Generic LDAP: This can be used with most any LDAP configurations. It exposes all supported options and allows for advanced configuration details to be provided. |
| Domain Name |
Set the “coerce” flag. This must be included if creating a backup on a non-admin server within a cluster. |
| LDAP | Details to be used for connecting to the LDAP server. This is configured as described below under LDAP Shared Configuration. Details to be used for connecting to the LDAP server. This is configured as described below under LDAP Shared Configuration. |
| User Search Base | This option represents the Distinguished Name of the LDAP element containing the users to be found. Note that the users may exist at any level in the LDAP tree below this element. Example: “ou=People,dc=edgeti,dc=com” |
| User Search Filter | This expression represents the LDAP search query that will be executed to search for one or more users. For OpenLDAP/Active Directory, this field default should be sufficient. Example: “&(objectClass=inetOrgPerson)(objectClass=customUserClass)” |
| Login Attribute | This represents the LDAP attribute of the user that will be used for login purposes. For OpenLDAP/Active Directory, the field default should be sufficient. Example: “uid” |
| Attributes to Cache | edgeCore can store attributes on the locally stored user entity (which refers to the LDAP user). Click + to add a new attribute that should be cached. |
Step 2: Preview User Search
Once the basic options have been specified, and an LDAP Shared Configuration has been specified (see below), Edge will provide an abbreviated preview of a number of users that exist in the LDAP repository.
Step 3: Roles
If the optional Group configuration is specified on the LDAP Shared Configuration, a Roles tab will appear on the left of the LDAP Domain configuration wizard. This permits the mapping of one or more LDAP groups to Edge roles. When users log in to Edge, their access within edgeCore will be driven off of LDAP membership.
Mapping LDAP Groups to Edge Roles
- To add a new mapping, click the
+icon in the panel’s footer. This will create a new mapping, which is shown as a new list item. - Select the LDAP Group using the drop-down on the left.
- Map that LDAP Group to an Edge Role using the drop-down on the right. If the Role does not already exist, click the
+icon to the right of the drop-down to create it.
LDAP Shared Configuration
As mentioned above, LDAP domains of the same basic LDAP type (AD, OpenLDAP, Generic) may share some configuration parameters. In this way, if a number of Domains need to be created relative to the same LDAP server, users can change connection settings in one place which will affect all Domains using that server.
Adding an LDAP Shared Configuration
From within the Domain configuration wizard, click the + icon beside the LDAP dropdown.

This will present the New LDAP Connection configuration screen:
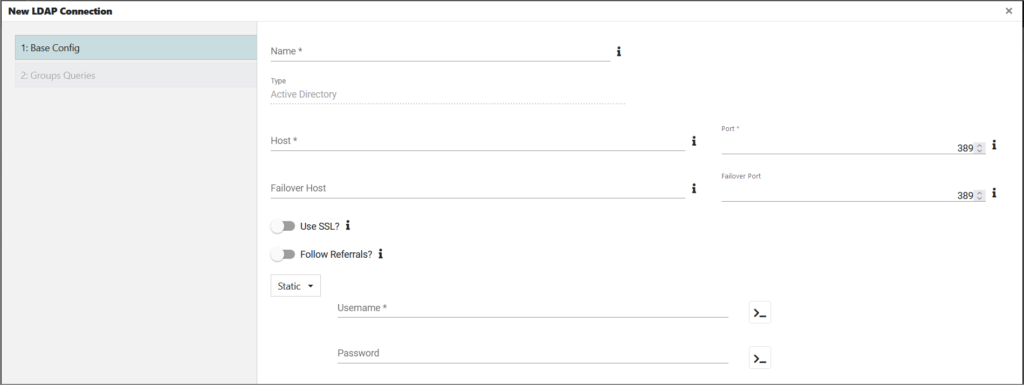
Step 1: Base Config
| Property | Description |
|---|---|
| Name | A symbolic name used to represent this shared configuration. This is the name that will appear in the pull-down for the LDAP field. |
| Type | The type of the shared configuration. This will default to the type of LDAP Domain that is being configured. |
| Host | The IP or hostname of the LDAP server. |
| Port | The TCP port of the LDAP server. |
| Use SSL? | If enabled, LDAPS will be used to communicate with the LDAP server. |
| Search User Credentials | Enter the distinguished name (DN) and Password of a user with permission to query the LDAP server. In order to configure LDAP users or map LDAP groups to Edge roles, edgeCore needs to be able to perform LDAP searches which require a valid username and password. This account should have read-only access to the information needed for the synchronization of users and roles. For example: Username = “cn=Manager,dc=edgeti,dc=com”. |
Step 2: Groups Queries
Edge LDAP Domains may optionally map one or more LDAP groups to Edge roles so that when users log in their access within edgeCore is driven off of LDAP membership. Thus, if the LDAP group membership should change, Edge will react to it without any additional local configuration changes. In order to enable this group mapping, navigate to the Groups Queries tab and set the Search for Groups property to Yes.
When Search for Groups is set to Yes, a few additional configuration options will be presented:
| Property | Description |
|---|---|
| Group Search Base | Similar to “User Search Base,” this option refers to the Distinguished Name of the LDAP element under which all groups may be found. Example: “ou=Groups,dc=edgeti,dc=com” |
| Group Search Filter | Similar to “User Search Filter,” this option defines the query that will be run to find one or more groups within the DN specified by Group Search Base. For OpenLDAP/Active Directory, this field default should be sufficient. Example: “&(objectClass=posixGroup)(objectClass=customGroupClass)” |
| Group Attribute | The LDAP group attribute that should be used to identify groups. Example: “cn” |
| Group Attribute for User Membership | Applicable only to OpenLDAP or Generic Directory. This option specifies the Group object’s attribute name that contains the dn of the member user. Example: “memberUid” or “member. |
| User Attribute for Group Membership | Applicable only to Generic Directory. This option specifies the User object’s attribute name that contains the dn of the member group. Example: “memberOf”. Either Group Attribute for User Membership or User Attribute for Group Membership needs to have a value. User Attribute for Group Membership will be ignored if there is a value set for Group Attribute for User Membership. |
EdgeCore 4.3.3 Version
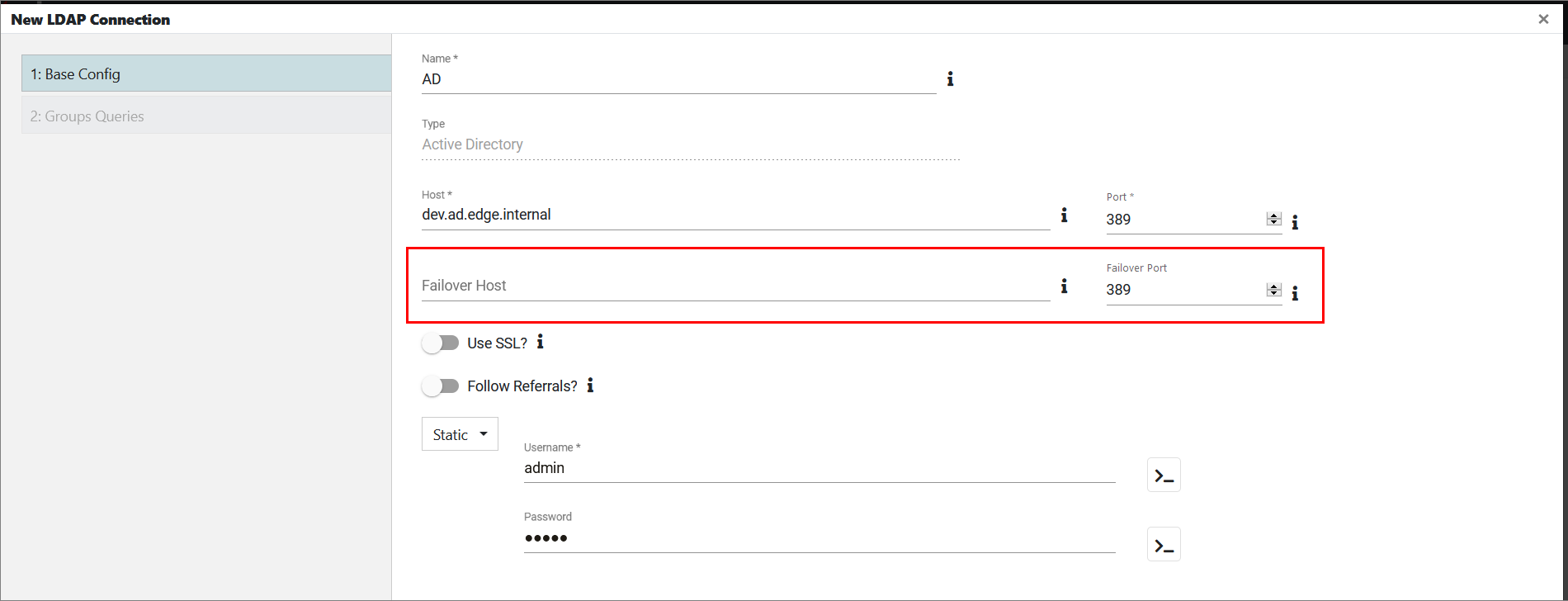
Handling Failover
Setting a failover host and port is done on the Base Config tab when creating a new LDAP connection.
Handling Referrals
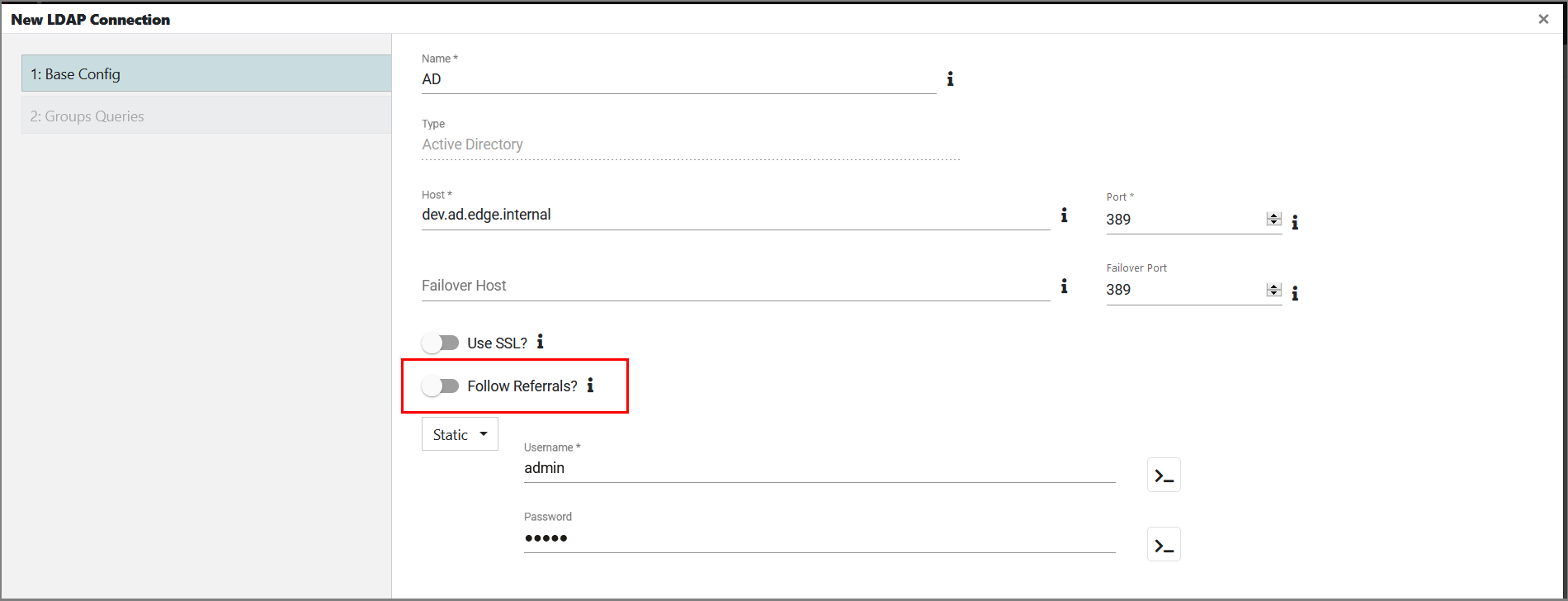
When creating a new LDAP connection, choosing whether or not to follow referrals is done by enabling/disabling the Follow Referrals toggle on the Base Config tab. By default, the toggle is disabled. Additionally, when enabled, Follow Referrals may slow authentication, but it is necessary with an LDAP forest network architecture.
Importing the CA Certificate into the SSL TrustStore
Follow these steps:
- Place the .cer file inside edgeCore install home/conf/ssl
- Create a terminal inside edgeCore install home/conf/ssl by running the following:
keytool -import -file certificatefilename -alias EdgeCore -keystore cacerts
- Set the password on the terminal. As a result, the cacert gets created.
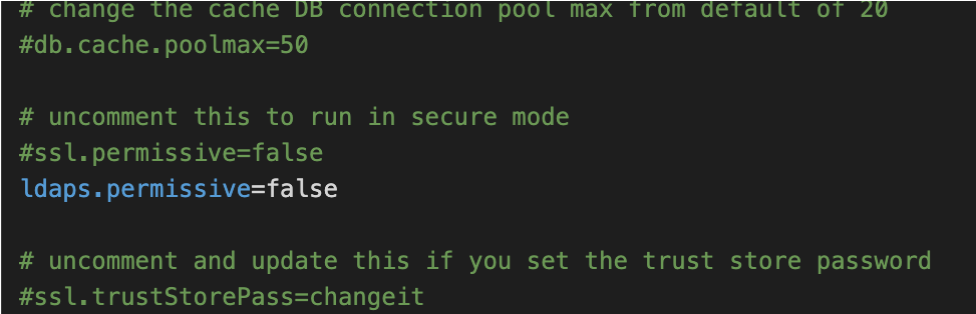
- In custom.properties (edgeCore install home/conf), make sure that ldaps.permissive=false
- Make sure that environment.sh (edgeCore install home/conf) is set up to only use the TrustStore: