To set up SAML in EdgeCore:
- Extract saml.zip (files will extract to SAML folder).
- Place customAuth.js from SAML/ in $EDGEHOME/scripts and change the file name to prevent accidental usage.
- Place login.egdejsp from SAML/ in $EDGEHOME/jsp and change the file name to prevent accidental usage.
- Places content from SAML/lib to $EDGEHOME/lib.
- Place content from SAML/tomcat into $EDGEHOME/tomcat.
- Create keystore by running: $PATHTOkeytool/keytool -genkey -keyalg RSA -alias edge -keystore saml.jks -validity 1095 -keysize 2048 (keytool is part of JDK and is usually located inside jdkFolder/contents/home/bin folder).
- Create a security-focused, strong password.
- Enter first and last name.
- Enter IT for the customer organizational unit.
- Enter company name when prompted for the organization.
- Enter address information for the city.
- Enter state.
- Enter two-letter country code.
- Confirm configuration [yes].
- Hit return to enter the key password for <edge>.
- Regenerate the keystore prior to expiration, 1095 days from the generation.
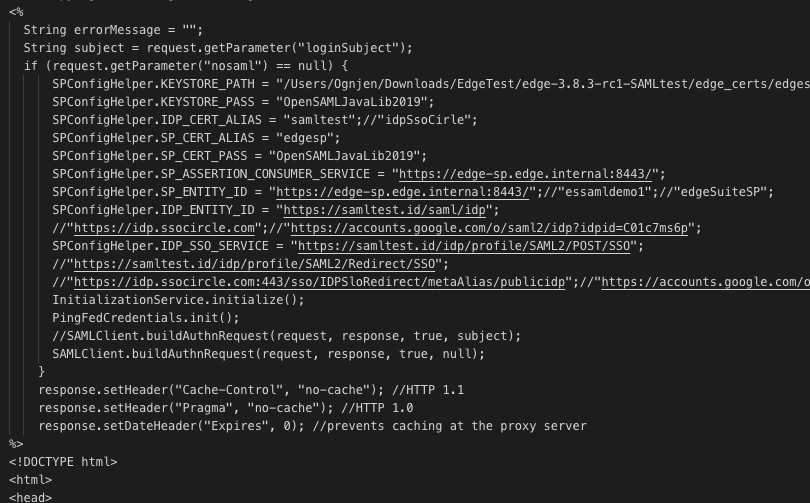
- Edit login.egdejsp that you transferred to $EDGEHOME/jsp:
a) KEYSTORE_PASS = “Value entered during generation”;
b) SP_CERT_PASS = “Same as KEYSTORE_PASS”;
c) SP_ASSERTION_CONSUMER_SERVICE = “edgeSuite URL”;
d) SP_ENTITY_ID = “edge-saml-$ENV”; (for example: prod, dev, test, etc)
e) SP_CERT_ALIAS = “edge”;
f) IDP_CERT_ALIAS = ‘idp’;
g) KEYSTORE_PATH = ‘$PATH to saml.jks’
h) IDP_ENTITY_ID = “https://test/idp”; (replace with your idp)
Here is a login.edgejsp example:
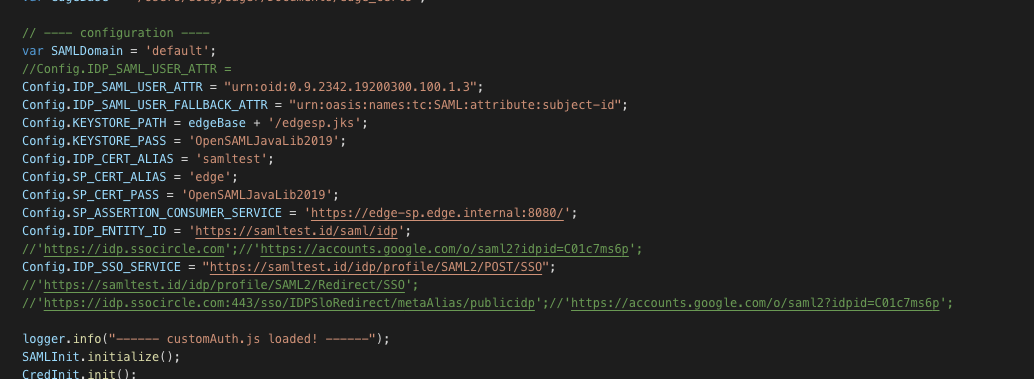
- Edit customAuth.js.whateveryouchangedthefilenameto
a) KEYSTORE_PASS = “Value entered during generation”;
b) SP_CERT_PASS = “Same as KEYSTORE_PASS”;
c) SP_ASSERTION_CONSUMER_SERVICE = “edgeSuite URL”;
d) SP_CERT_ALIAS = “edge”;
e) IDP_CERT_ALIAS = ‘idp’;
f) KEYSTORE_PATH = ‘$PATH to saml.jks’
Here is a customAuth.js example:
- Create metadata by executing $PATHTOkeytool/keytool -keystore saml.jks -export -alias edge -file /tmp/edge.crt -rfc (keytool is part of JDK and is usually located inside jdkFolder/contetnts/home/bin folder)
a) Enter keystore password when prompted.
b) File will be generated at a specified location. - Create metadata at https://www.samltool.com/sp_metadata.php
a) Set EntityId to same value as SPConfigHelper.SP_ENTITY_ID (ex: edge-saml-$ENV).
b) Set Attribute Consume Service Endpoint (HTTP-POST) to same value as SPConfigHelper.SP_ASSERTION_CONSUMER_SERVICE (ex: edgeSuite URL).
c) Set AuthnRequestsSigned to true.
d) Set WantAssertionsSigned to true.
e) Copy Certificate file contents from step 18 into SP X.509 cert (same cert for sign/encrypt)
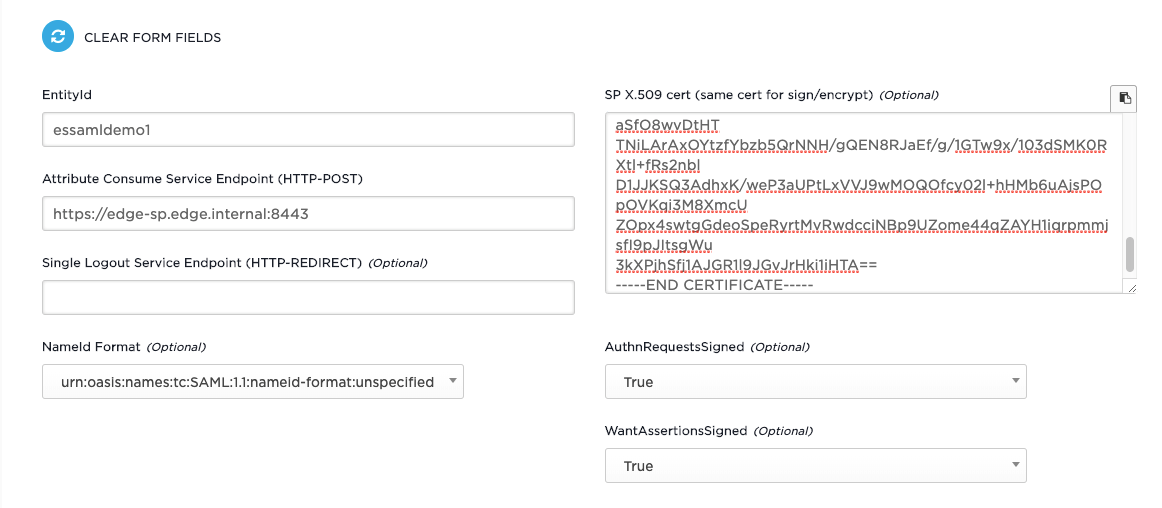
f) Scroll down and click Build SP Metadata.
g) Select all from the resulting SP METADATA text box, and drop it in a text editor.
h) Change validUntil to add an additional month beyond the generated value.
i) Save changed Metadata text as edge.xml and send to IdP admin along with the request for IdP metadata.
Here is an example of metadata XML:
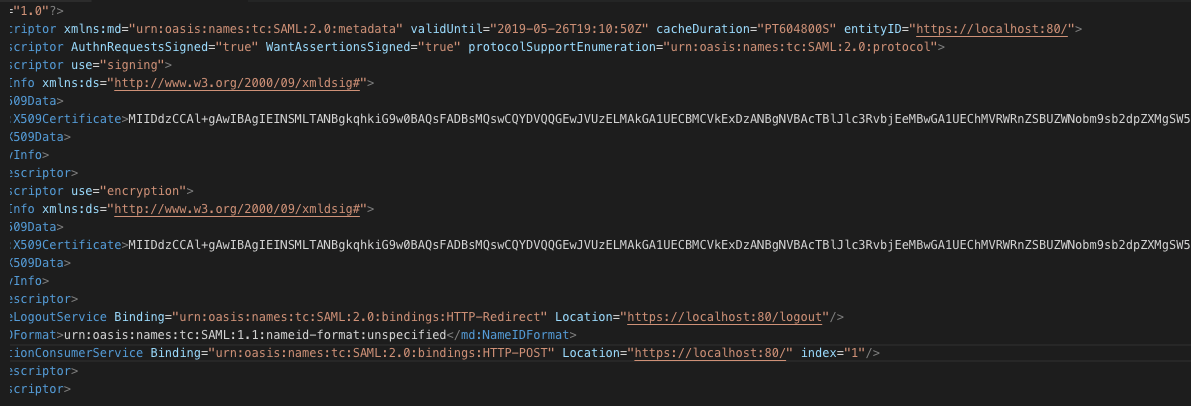
j) Edit login.egdejsp.whateveryouchangedthefilenameto and customAuth.js.whateveryouchangedthefilenameto with the information provided by the customer:
– IDP_ENTITY_ID maps to EntityDescriptor entityID=”$VALUE” in the IdP metadata
– Config.IDP_SSO_SERVICE maps to the location of the SingleSignOnService Binding, provided the binding is HTTP-POST
k) Copy the certificate value where KeyDescriptor use=”signing” from the customer IdP xml into a new text editor file
It should be approximately 900 characters. Break the certificate value text down into 76 character lines. (If there are spaces in the certificate value, place the new lines there)
l) Add —–BEGIN CERTIFICATE—– before the certificate value and —–END CERTIFICATE—– afterward. It should look like this:
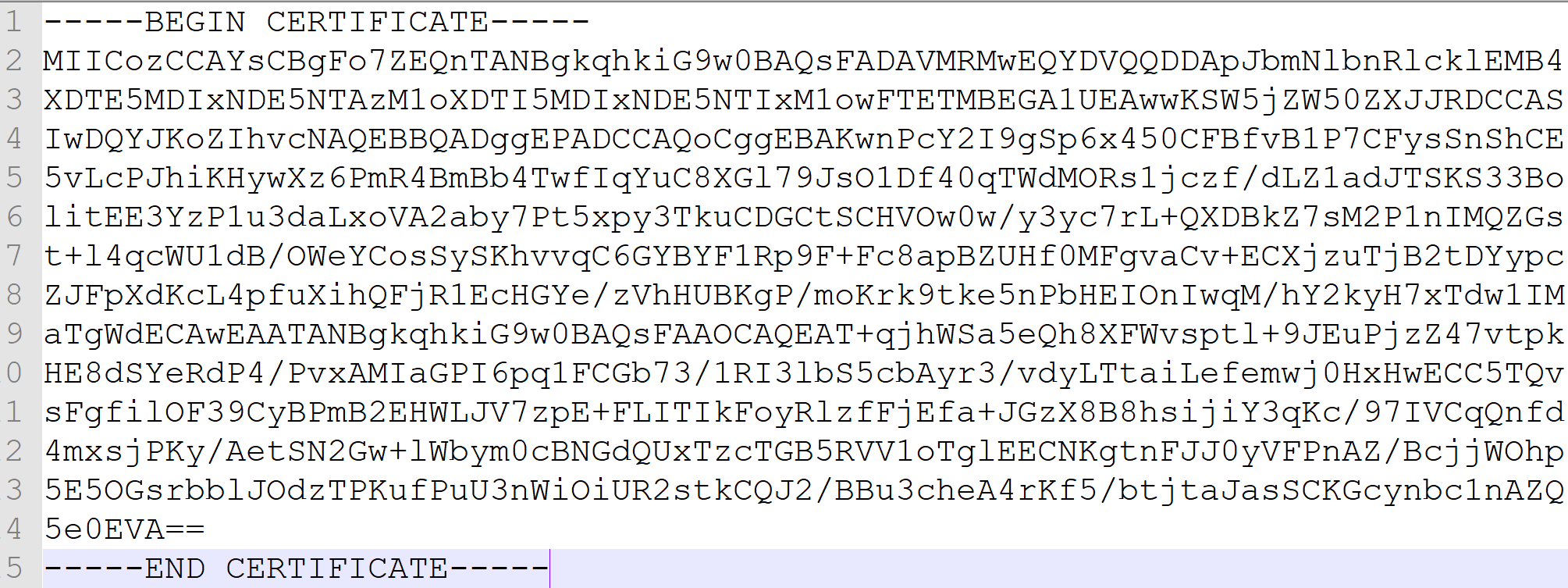
m) Save as <CertName>.crt.
n) Run keytool -import -keystore saml.jks -file $WhereeverYouStoredIt/idp.crt -alias idp
o) When it prompts you for the password, use the same as stored in the login.egdejsp file as SPConfigHelper.KEYSTORE_PASS
p) Say yes when it prompts you to trust the certificate.
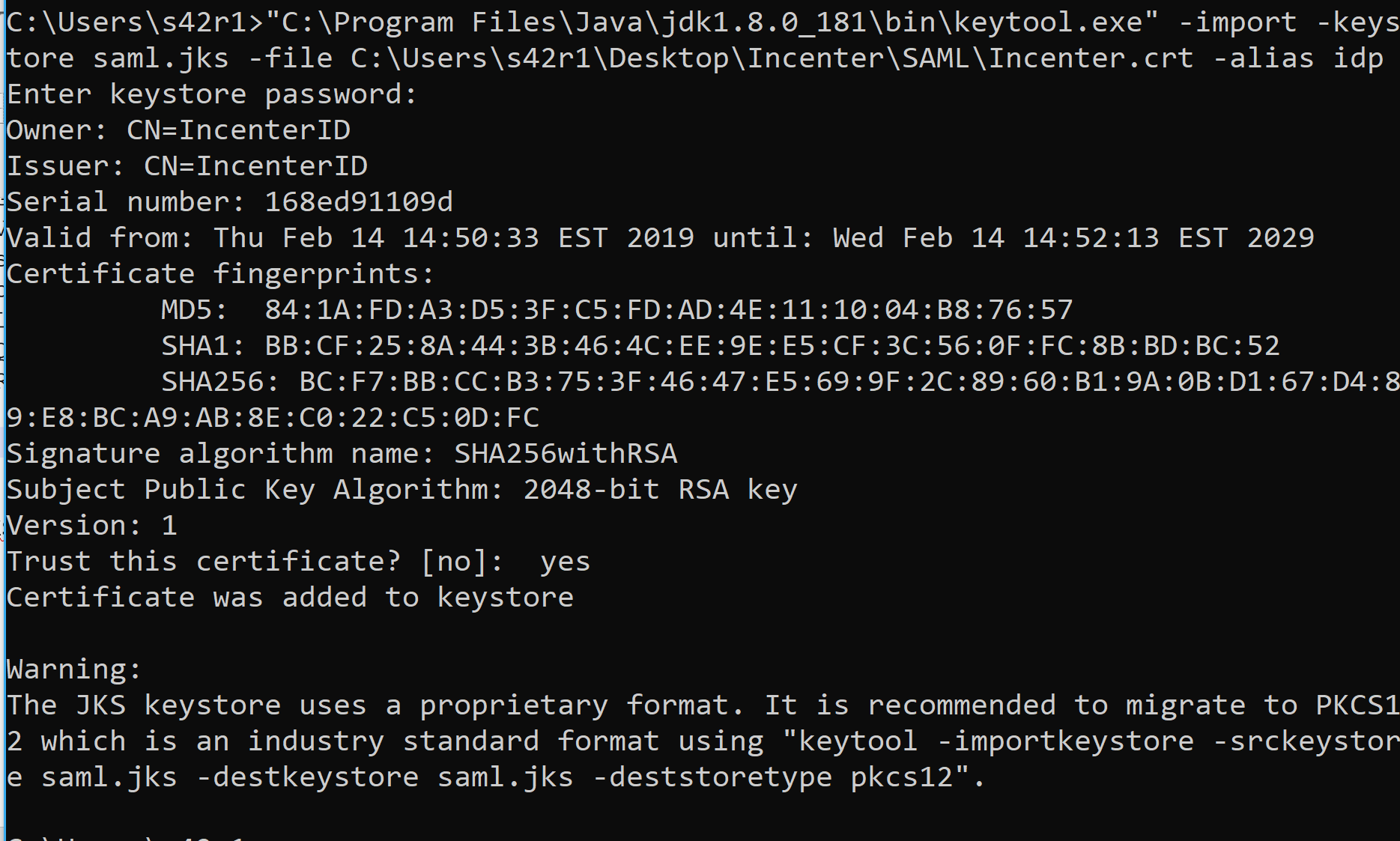
- Rename customAuth.js.whateveryouchangedthefilenameto in $EDGEHOME/scripts to customAuth.js
- Rename login.egdejsp.whateveryouchangedthefilenameto in $EDGEHOME/jsp to login.egdejsp
- Cycle EdgeCore to incorporate changes.
