Overview
edgeCore integrates with CyberArk’s Password Vault to look up credentials for privileged accounts that are maintained and managed by CyberArk. Rather than having an Administrator who is responsible for knowing a privileged account credential, CyberArk is used to manage the account. edgeCore is then able to use CyberArk’s PSDKPassword Java Library to read the privileged account credentials when it needs to authenticate. Authentication may be against Data Source or LDAP servers for example. Using this API, the privileged account credentials are more secure and passwords that are changed periodically will not affect edgeCore as it has control logic to wait for password changes to complete when looking up credentials. Another benefit is that administrators will not be required to edit connection settings when passwords expire and reset.
edgeCore provides the ability to insert CyberArk Password Vault Expressions in security variables that will be evaluated at the point of usage. The CyberArk Credentials are looked up via a keychain that references a configured set of key/value parameter pairs. The lookup must evaluate to a unique entry. It is important for you to get the information necessary to generate named Keychains that will be used to look up credentials. Keychains are currently registered via config/password_vault/cyberark.properties with the following convention:
password.vault.keychains.keychainAlias.appid=oracleDB
password.vault.keychains.keychainAlias.policyid=
password.vault.keychains.keychainAlias.safe=edgeCore
password.vault.keychains.keychainAlias.folder=root
password.vault.keychains.keychainAlias.object=edgeCoreUser
password.vault.keychains.keychainAlias.database=
password.vault.keychains.keychainAlias.address=
password.vault.keychains.keychainAlias.username=
Note: The configuration must have a uniquely named keychainAlias and you will also be required to include at least the following: appid, safe, folder, and object. The folder will default to ‘root’ if not specified. You may also need to provide these other settings: policyid, database, address, and/or username if they are necessary to identify a unique password vault entry.
Install the CyberArk Agent
Installation of the CyberArk agent local to the edgeCore server is required. The agent provides several different SDKs to enable access of credentials managed by the Password Vault. The agent manages caching of the passwords and also knows when passwords are being reset. This allows for the edgeCore integration to make requests and even retry requests when CyberArk responds with a PasswordExpired error. To install the CyberArk Agent, please refer to the CyberArk PAS Solution (AIM). AIM includes the CyberArk Application Password Provider and SDKs for the different supported interfaces. Download “Credential Provider & OPM-Rls-9.6.zip” from the “Root\v9.6\PAS Components\AIM & OPM CD Image” Folder. Within the compressed ZIP file you will find the different distributions of the Credential Provider. Pick the installation you need based on your OS environment.
Please refer to CyberArk’s AIM installation and configuration manuals when configuring it in your environment.
Install the PSDKPassword Java Library
Once the CyberArk Password Provider and SDKs are installed, you will need to ensure edgeCore has the PSDKPassword.jar library included in its classpath. Either copy PSDKPassword.jar into edgeCore’s /lib directory; or it must be included on the classpath (via /conf/environment.(sh|bat)). The required library is found on Windows installations at C:\Program Files (x86)\CyberArk\ApplicationPasswordSDK\JavaPasswordSDK.jar.
UNIX: add the following line with the proper path in conf/environment.sh:
CLASSPATH=/opt/.../JavaPasswordSDK.jar
Windows: add the following line with the proper path in conf/environment.bat:
set "CLASSPATH=%CLASSPATH%;C:\Program Files (x86)\CyberArk\ApplicationPasswordSDK\JavaPasswordSDK.jar"
Register a Keychain
Keychains are registered by inserting the following block into the conf/cyberark.properties file and updating the keychainAlias with a name that will be used to refer to the credentials that will be looked up. The conf/cyberark.properties file must be created when the first keychain is registered.
password.vault.keychains=keychainAlias
password.vault.keychains.keychainAlias.appid=oracleDB
password.vault.keychains.keychainAlias.policyid=
password.vault.keychains.keychainAlias.safe=edgeCore
password.vault.keychains.keychainAlias.folder=root
password.vault.keychains.keychainAlias.object=edgeCoreUser
password.vault.keychains.keychainAlias.database=
password.vault.keychains.keychainAlias.address=
password.vault.keychains.keychainAlias.username=
1) Replace ‘keychainAlias’ with the alias to be used to reference these credentials. Each keychain requires this line so the Expressions User Interface will report it when prompting the user to pick an expression.
2) Fill in the key/value pairs necessary to look up a unique credential from CyberArk. Note: appid, safe, and object are required. The folder defaults to ‘root’ if it is not set.
Applying a Keychain
When setting up a Data Source Connection or an LDAP Connection you may want to apply credentials; please see the following two sections that provide some example ways this can be configured.
- Adding a CyberArk “Expression” to a Data Source Connection
- Creating a CyberArk Expression backed Credential
When configuring expressions to be used for credentials, you will see them displayed in the format of: info.cyberark.keychainAlias.token. The keychainAlias refers to any of the keychains registered in config/password_vault/cyberark.properties. The token will typically be either be username or password, but the following are all valid options: password, content, username, database, policyid. Note: <b>password</b> and <b>content</b> are aliases; both evaluate to the password.
If you do not see a registered keychain please review the cyberark.properties file and ensure it has the proper permissions set.
Adding a CyberArk “Expression” to a Data Source Connection
CyberArk Expressions are used for server-side filtering or qualification of data, such as filtering a query of tickets by a customerId of a ticket. These can be used like Node Variables, but the Secured Variables are assigned values based on the identity of the User – either the User’s directly assigned value or a Domain-assigned value.
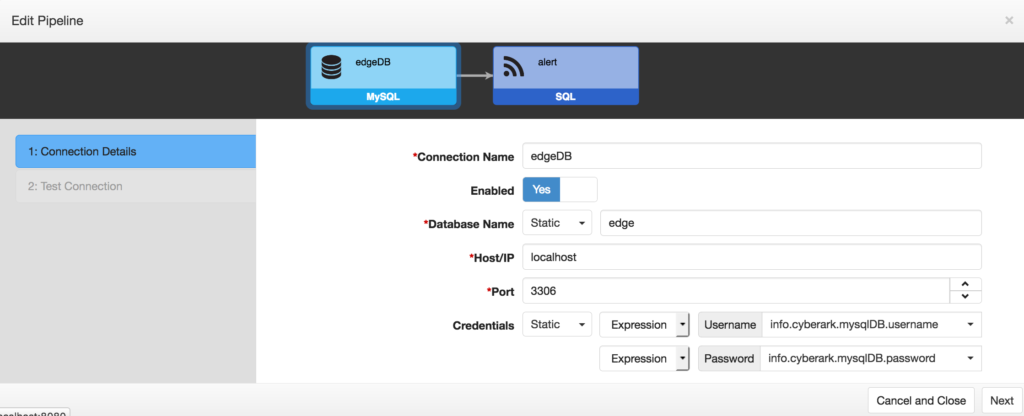
For “Static” credential values, the following properties are available:
| Property | Description |
|---|---|
| Name | Symbolic name to use for this Variable. This label will be displayed on the User and Domain Provisioning views. |
| Static or Variable? | Determines whether this credential is configured separately and can be shared with other connections. 1. Static: Enables the Username and Password input. Requires a selection of whether the value will be a Static or an Expression. After selecting Expression you will have a list of valid options to choose from what includes the registered CyberArk keychain aliases. 2. Variable: Disables the Default Value input. This option required a selection of managed credentials. |
Creating a CyberArk Expression backed Credential
If a keychain alias will be used multiple times, you should create a new Credential. This can be done directly when registering a new connection, by clicking the “Add” Button after selecting Variable instead of Static.
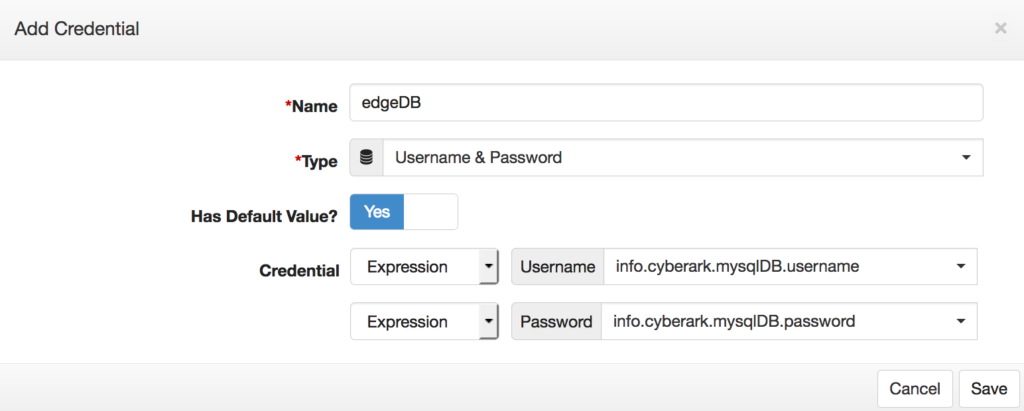
For “Static” credential values, the following properties are available:
| Property | Description |
|---|---|
| Name | Symbolic name to use for this Credential. This label will be displayed on the Credential selection dropdowns and also in the defaults Credentials views. |
| Type | 1. Username and Password 2. Username, Password and Domain |
| Has Default Value? | Yes – Enables the Username and Password input, providing the option to select whether the value is a Static or Expression. |
| Static or Expression | Determines whether this credential is configured separately and can be shared with other connections. Static: Username and Password inputs are entered directly. Expression: This option enables the selection of a CyberArk Expression for any of the registered keychain aliases. |